What is DDoS attack and how it works?
There are many different types of attacks executed from hackers to destroy or to gain access to some critical information. This is a kind of attack which stops a website or compels the server to overload. “DoS” stands for Denial of Service, i.e. the “refusal of a service”. A DDoS stands for Distributed Denial of Service attack. In this article we will see in details What is DDoS attack and How it works?
Why DDoS attacks are done?
DDoS attacks aim to bring down servers or web services. In order for a server to go “down”, it must be overloaded. It always works the same way with DDoS attacks. The server (e.g. that of a website or an e-mail service) is overwhelmed with so many requests that it can no longer keep up with answering these requests. The attack consists of simply overloading the server programmed to respond and thus making a website inaccessible to other users.
The hackers usually demand a ransom from the affected company so that its system and services can be accessed again by its customers. Hackers have changed the DDoS attack over the years. There are various ways of causing DoS attacks.
How do DDoS attacks work?
DDoS attacks can overload the server in various ways. An example is the so-called SYN flood attack. When we visit a website from our computer, the server (website) and client (requesting computer) carry out a so-called three-way handshake. Normal flow of a three-way handshake looks like this
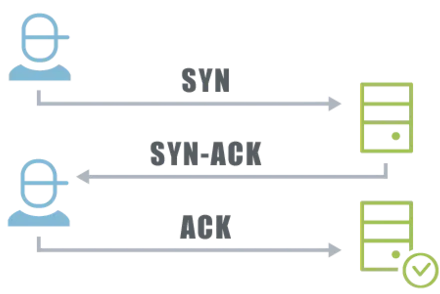
- The client sends a synchronization request to the server (SYN = synchronize)
- The server replies to the client with a confirmation SYN, ACK, which confirms the synchronization (ACK = acknowledge)
- The client also confirms this process with a ACK then the connection is now established.
How hackers do it?
Hackers who want to cause a server to crash omit the final acknowledge (ACK) response. The attacker floods the server with SYN requests and in the next step suppresses the ACK confirmation.
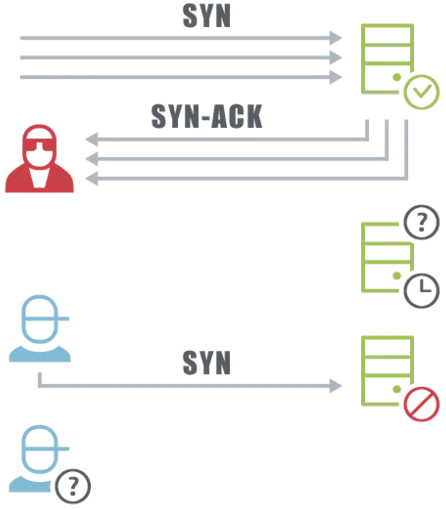
For each request, the server waits a while before terminating the connection, as it only assumes there will be a delay. Storage and computing resources of the server are used for this. This is not a problem with a few requests from clients.
If thousands of request arrives at the server at the same time, the server’s resources are quickly used. No other client can then make a request, for example to a mail server. Although you are waiting for an important reply from a colleague, log into your mail account and press “Enter”, all that appears is: “Service temporarily unavailable”, – denial of service (DoS).
Strictly speaking, a SYN flood attack is “only” a DoS attack, since it can theoretically be launched from just one computer. The SYN flood reflection attack is a modified form in which an attacker recruits other uninvolved servers for the attack. It sends SYN requests to multiple servers, which respond with multiple SYN/ACK packets.
So not directly to the victim. The SYN/ACK responses from these servers are then redirected to the victim’s server. The attacker simply spoofs the IP address and makes the attacking servers believe that the requests are being sent from the victim’s server. Now the co-attacking servers flood the victim with their response packets, causing him to become overloaded.
Traditionally, DDoS attacks are always launched from an entire network of computers. Botnets are particularly well suited for attackers and this also makes it clear what the “D” in DDoS stands for, namely for “distributed”.
Botnets and the Internet of Things
Does your fridge have WiFi? Probably not. But your printer certainly will. In fact, it’s possible that he’s been an accomplice in a distributed denial-of-service attack before. Of course not voluntarily. Attackers who want to bring companies like Twitter or Facebook to their knees with DDoS attacks use botnets. A created botnet leads to massive requests to the server crash.
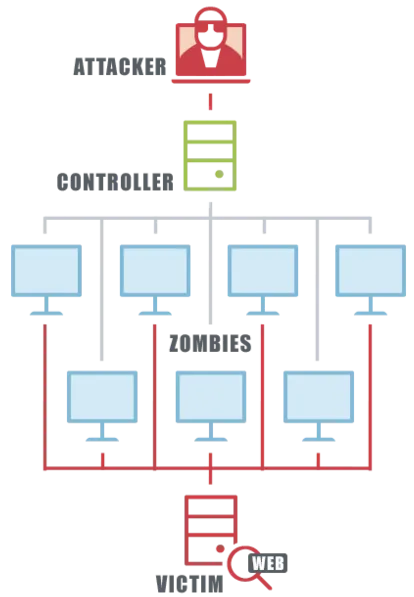
In order to carry out DDoS attacks, the attackers first set up a botnet on the Internet, which then directs the requests to the target server for them. Botnets are created by installing malware on the “zombie machines”. A small part of their computing power is squandered to carry out commands for the attacker.
The planned DDoS attacks are then carried out using the compromised computers. They are ordered to shower the target server with SYN requests, for example. If the botnet system is large enough, the target server will collapse and the associated website will stop working.
Computers usually have the appropriate software, such as a firewall, to prevent them from being used by DDoS attackers. However, hackers have it easy in the ever-expanding Internet of Things (IoT). They hack anything that can make a request to a server for DDoS attacks. Printers, routers, lawnmowers running with default settings and no firewall are easy prey.
Must Read:
- Keeping you server safe from SSL and TLS vulnerabilities
- Different Types of Processor Socket in Motherboard
Real Attacks
On October 21, 2016, there was a breakdown in the USA: Twitter, Airbnb, Spotify, Reddit, Ebay and other online services, including Netflix, were no longer available for over two hours. You have been the victim of a DDoS attack. Basically, DoS describes the failure of a website due to overload.
The servers of the individual companies were not the direct target of the attackers. All of these companies are customers of DNS (Domain Name System) provider Dyn in the US state of New Hampshire, which has been the victim of a massive attack. Read here how DDoS attacks work and what your printer or even your smart refrigerator could have to do with it.
Mirai botnet
The Mirai botnet carried out the attack on Twitter and Co. on October 21, 2016 in the USA. Dale Drew, chief security officer at Level 3, an ISP, found evidence that around 10 percent of all devices co-opted by Mirai were used to attack Dyn’s servers. A week earlier, Level 3 found that 493,000 devices were infected with Mirai malware, almost doubling the number from last month.
How can companies protect from DDoS attacks?
This is basically quite simple: A company can obtain so much capacity through service providers that even large quantities of inquiries can always be processed and no collapse occurs. Because the capacity of the target server is the decisive point in an attack. This can be done using cloud services that quickly add capacity when traffic increases.
Another way is to set up a filter system. Here, the traffic is no longer processed via a company’s own server, but pre-sorted in a so-called “scrubbing center”. Only clean traffic is then forwarded to the server in the company itself.
Scrubbing centers analyze the traffic and filter out possible DDoS attacks. Typical patterns of DDoS attacks are recognized and an attack on the company’s server becomes impossible. Because the denial of service, the refusal of service, only happens if the company server crashes. Then it can no longer be reached directly for the attack.
SYN cookies are another way to mitigate DDos attacks. With the three-way handshake, a TCP protocol (Transmission Control Protocol) is always created by the server. During DDoS attacks, this is always left in an open state in order to deprive the victim server of storage resources.
SYN cookies prevent this mechanism by sequencing the number of SYN/ACK requests and responses. In this way, the attacked server does not have to find any storage space for storing the half-open TCP tables and is not overloaded so quickly.
We hope you like this article about What is DDoS attack and How it works? Please do share this article with others to make them understand about this kind of attacks.