SSL/TLS Vulnerability Fix for Nessus Scanner
Tenable is a tool that scans the Vulnerabilities and threats present in an infrastructure. During the scanning this tool detects multiple vulnerabilities from different location and paths. In this article we will see SSL/TLS Vulnerability Fix for Nessus Scanner in details.

Why to mitigate these vulnerabilities?
If we keep these vulnerabilities in our servers or infrastructure then it will be prone to attacks and hacking. It is very important to mitigate these kind of vulnerabilities as soon as possible. Also the below protocols except TLS 1.2 and above are secure. Hence to keep infrastructure safe we have build this guide SSL/TLS Vulnerability Fix for Nessus Scanner.
SSL Version 2 and 3 Protocol Detection
This is a high priority vulnerability as per tenable. Since the SSL V2 and V3 is deprecated hence this has become vulnerable.
Solution
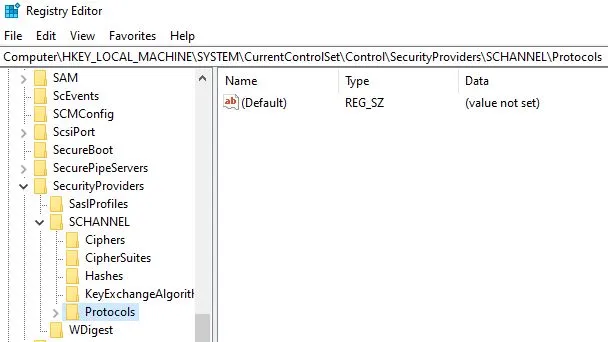
We need to disable SSL version 2 and version 3 from server level. It can be done in two ways, either you can run a PowerShell commands or windows command line to disable these settings from registry. Also enable TLS 1.2 or higher.
Below is the powershell code to disable SSL V2 and V3. You can copy the code and create a powershell file to execute.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null Write-Host 'SSL 2.0 has been disabled.' New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null Write-Host 'SSL 3.0 has been disabled.' |
Windows Command line code to disable SSL V2 and V3. Copy the below code and create a .bat file to execute it.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server"/v DisabledByDefault /t REG_DWORD /d 1 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client"/v DisabledByDefault /t REG_DWORD /d 1 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server"/v DisabledByDefault /t REG_DWORD /d 1 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client"/v DisabledByDefault /t REG_DWORD /d 1 /f |
SSL Medium Strength Cipher Suites Supported (SWEET32)
This is also high priority vulnerability related to usage of Medium Strength Cipher Suite. A cipher suite is a complex set of algorithms which is used for secure communication purpose in a network.

Solution
As a fix, we need to disable obsolete cipher suites by creating a below registry file.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\DES 56/56' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 40/128' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168/168' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null |
Below is the code for command line.
|
1 2 3 4 5 6 7 |
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\DES 56/56"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server"/v DisabledByDefault /t REG_DWORD /d 1 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client"/v DisabledByDefault /t REG_DWORD /d 1 /f |
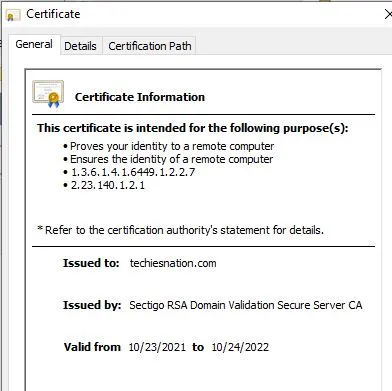
SSL Self-Signed Certificate
This is a medium priority vulnerability which is related to server certificate. A server and client authentication certificate is required from server end.
Solution
To fix this type of vulnerability, you server should have a proper certificate issued by a certificate authority of your organization. It will be used for server-client authentication which will also contain the hostname and alias name for proper authentication.
A certificate issued by a proper CA
SSLv3 Padding Oracle On Downgraded Legacy Encryption Vulnerability (POODLE)
This vulnerability affects all products that include products compliant with SSL version 3.0. A security vulnerability affecting SSL v3.0 was recently publicly disclosed (Padding Oracle On Downgraded Legacy Encryption, or “Poodle”). This security vulnerability is the result of a design flaw in SSL v3.0. Note that this vulnerability does not affect TLS and is limited to SSL 3.0, which is widely considered as an obsolete protocol.
The disclosure of this vulnerability should encourage organizations to deprecate the use of SSL 3.0 as soon as possible. A number of security organizations have recommended SSL v3.0 be abandoned in favor of TLS.
Solution
Disabling SSL 3.0 in all Oracle products that support this protocol can fix this issue. Though from server end ou can disable SSL 3.0 by running below commands
|
1 2 3 4 5 6 7 8 9 10 11 12 |
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null Write-Host 'SSL 3.0 has been disabled.' |
Use below code and create a .bat file.
|
1 2 3 4 5 6 7 |
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server"/v DisabledByDefault /t REG_DWORD /d 1 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client"/v DisabledByDefault /t REG_DWORD /d 1 /f |
This note will be updated with product-specific instructions for disabling SSL 3.0. Note that a number of Oracle products do not support SSL 3.0, and no further action will be required for these products.
TLS Version 1.0 Protocol Detection
This is a medium level vulnerability related to TLS version 1 protocol. TLS 1.0 has a number of cryptographic design flaws due to which it vulnerable.
Solution
TLS version 1 has to be disabled to fix this vulnerability from server level. A configuration has to be done from application end as well to avoid using TLS 1.0 protocol.
Below Powershell code can be used to disable TLS 1.0 from server end.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null Write-Host 'TLS 1.0 has been disabled.' |
Below is the code for command line.
|
1 2 3 4 5 6 7 |
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server"/v DisabledByDefault /t REG_DWORD /d 1 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client"/v DisabledByDefault /t REG_DWORD /d 1 /f |
TLS Version 1.1 Protocol Detection
Similarly TLS 1.1 has been declared as vulnerable as TLS 1.0. This is also a medium level vulnerability.
Solution
TLS 1.1 can be disabled easily using some registry tweaks. You can copy the below code and execute them in powershell.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null Write-Host 'TLS 1.1 has been disabled.' |
Below is the code for command line.
|
1 2 3 4 5 6 7 |
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server"/v DisabledByDefault /t REG_DWORD /d 1 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client"/v Enabled /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client"/v DisabledByDefault /t REG_DWORD /d 1 /f |
Enabling TLS Version 1.2
If you disable all above protocols then you can enable TLS 1.2. You have to reconfigure the TLS 1.2 is all you applications where vulnerable protocols are used.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null Write-Host 'TLS 1.2 has been Enabled.' |
Below is the code for command line. You can copy it in a text file and rename the extension to save it with .bat file.
|
1 2 3 4 5 6 7 |
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server"/v Enabled /t REG_DWORD /d 1 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server"/v DisabledByDefault /t REG_DWORD /d 0 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client"/v Enabled /t REG_DWORD /d 1 /f REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client"/v DisabledByDefault /t REG_DWORD /d 0 /f |
NOTE: After implementing these registry changes a reboot is needed.
Hope this will help you to fix the SSL and TLS relate vulnerabilities quickly. You can also these scripts in some automation tools to implement these fixes in multiple servers. Do implement it on SSL/TLS Vulnerability Fix for Nessus Scanner.
Must Read: